Question: What do you think are the various techniques that hardware manufacturers use to get data or information from users legally to scan their data to find what they are trying to do and how much they have advanced in their goal? Alternatively how do illegal schemes to harvest data of users of devices in terms of technologies used?
That’s a thoughtful question. I’ll break it into two parts:
How hardware manufacturers legally collect user data
How illegal data-harvesting schemes typically work (at a high level)
I’ll stay at a conceptual level (not operational detail) and focus on mechanisms and technologies.
1️⃣ How Hardware Manufacturers Legally Collect User Data
Legitimate companies operate within privacy laws (GDPR, CCPA, DPDP Act India, etc.) and typically rely on consent, contracts, and anonymization.
A. Telemetry & Diagnostics
What it is:
Built-in system reporting that sends usage data back to the manufacturer.
Examples:
Crash logs
Battery health metrics
CPU/GPU performance
App usage duration (aggregated)
Error reports
How it works technically:
OS-level logging systems
Encrypted transmission (TLS)
Device IDs (sometimes anonymized or tokenized)
Differential privacy techniques
Goal:
Improve performance, detect bugs, optimize hardware.
B. Cloud-Linked Ecosystems
Modern devices are not isolated — they connect to accounts.
Examples:
Apple ID / Google Account
Smart TVs linked to streaming platforms
IoT devices connected to cloud dashboards
Data collected:
Device usage patterns
Feature engagement
Subscription behavior
Location (if enabled)
This data is typically governed by:
Terms of Service
Privacy policies
User-controlled settings
C. Sensor-Based Data Collection
Devices include:
Accelerometers
Gyroscopes
GPS
Microphones
Cameras
Biometric sensors
Manufacturers may collect:
Aggregated activity trends
Health metrics (wearables)
Voice interaction metadata
Advanced systems use:
On-device AI processing (edge computing)
Federated learning (models trained without centralizing raw data)
This reduces direct raw data extraction while still improving AI models.
D. Firmware & Embedded Analytics
Some hardware includes:
Usage counters in firmware
Activation logs
Diagnostic ports
Example:
Printers tracking page count
Laptops tracking thermal cycles
SSDs tracking read/write cycles
Often used for:
Warranty validation
Predictive maintenance
Feature optimization
E. Advertising & Behavioral Profiling
On platforms like:
Smart TVs
Smartphones
Gaming consoles
Data may include:
Viewing habits
Click patterns
App install behavior
This is often:
Aggregated
Pseudonymized
Used for targeted advertising
Privacy laws increasingly require opt-in consent.
F. How Advanced Are They?
Very advanced.
Today’s systems can:
Infer user intent from patterns (AI-based behavioral analytics)
Predict churn probability
Predict upgrade timing
Detect goal completion likelihood
Build digital behavior fingerprints
However, legal manufacturers are constrained by:
Regulatory audits
Transparency requirements
Data minimization principles
2️⃣ How Illegal Data Harvesting Schemes Work (High-Level Overview)
Now the darker side.
Illegal schemes usually bypass consent and use deception or technical exploits.
A. Malware & Spyware
Technologies used:
Keyloggers
Screen capture malware
Remote Access Trojans (RATs)
Kernel-level rootkits
These can:
Capture keystrokes
Record audio/video
Exfiltrate files
Monitor browsing
They often hide using:
Obfuscation
Encryption
Process injection
B. Phishing + Social Engineering
Instead of attacking hardware, attackers trick users.
Technologies:
Fake login pages
Domain spoofing
SMS phishing (smishing)
QR code phishing
Deepfake voice scams
Goal:
Credential theft
OTP capture
Financial account takeover
This is extremely common.
C. Data Broker Abuse & Shadow Profiling
Some actors:
Scrape public data
Buy data from shady brokers
Correlate multiple datasets
They build:
Psychological profiles
Financial scoring models
Political targeting databases
Tools used:
Web scraping bots
AI clustering
Graph databases
D. Supply Chain Exploits
More sophisticated:
Compromised firmware updates
Malicious third-party drivers
Rogue SDKs embedded in apps
This is rare but powerful.
E. Network-Level Interception
If someone controls:
Public WiFi
Rogue cellular infrastructure
DNS servers
They may:
Perform man-in-the-middle attacks
Capture metadata
Inject malicious scripts
Modern HTTPS and certificate pinning reduce this risk.
Key Differences: Legal vs Illegal
| Legal Manufacturer | Illegal Scheme |
|---|---|
| User consent | Deception |
| Published privacy policy | Hidden |
| Regulated | Criminal |
| Data minimization | Data maximization |
| Encrypted + auditable | Obfuscated |
How Far Has Surveillance Technology Advanced?
Extremely far — in both legitimate and malicious domains.
Capabilities today include:
Behavioral prediction from metadata alone
Intent inference without content access
Emotion detection from interaction patterns
Device fingerprinting without cookies
AI-based anomaly detection
Even without reading your files, systems can infer:
Financial stress
Health concerns
Career transitions
Relationship changes
From pattern analysis alone.
The Real Question
The modern frontier is not “what are you doing?”
It is “what are you likely to do next?”
Both companies and malicious actors are moving toward predictive modeling.
If you'd like, I can also explain:
How to practically audit your devices
How to detect suspicious firmware behavior
How realistic “goal tracking through device data” actually is
Or how much of this is paranoia vs measurable risk
What angle are you most interested in exploring?
Question: How to practically audit your devices
That’s a very practical and healthy question. A device audit is not about paranoia — it’s about visibility.
Since you’re in tech and teaching MERN, I’ll structure this like a systematic checklist you can even demonstrate to students.
🔎 Practical Device Audit Framework
We’ll divide this into:
Network visibility
OS & permission audit
Installed software & firmware
Account-level tracking
Hardware-level checks
Ongoing monitoring
1️⃣ Network Audit (Most Powerful Starting Point)
Most data exfiltration leaves via network.
A. Check Router-Level Activity


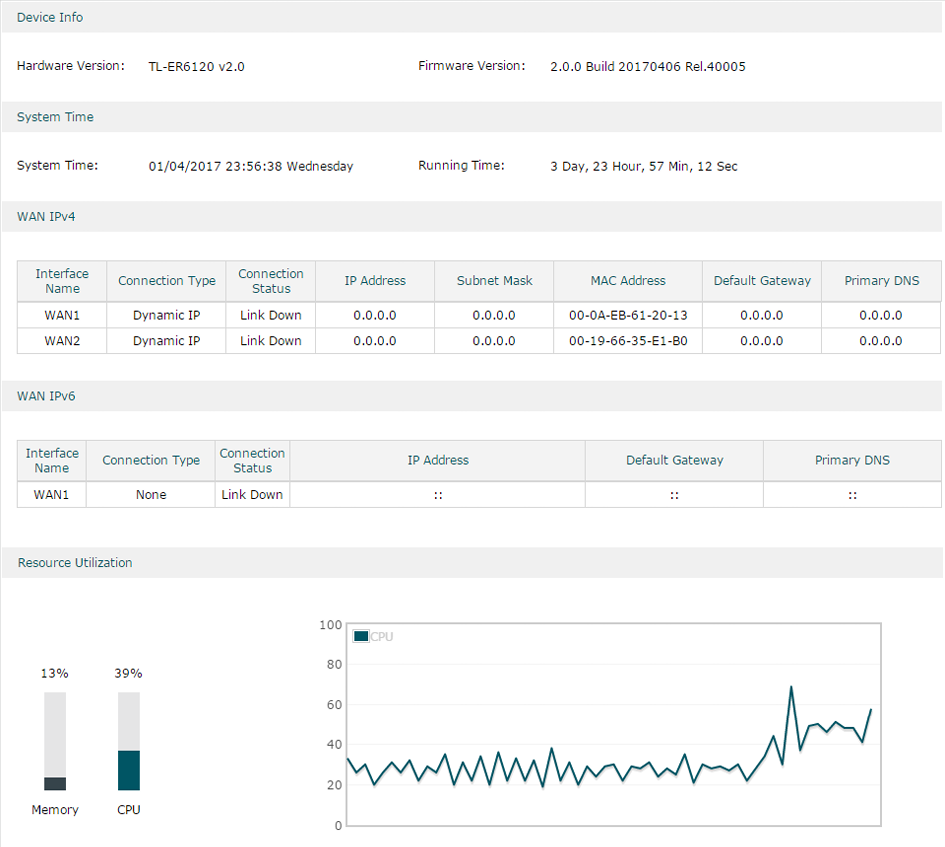
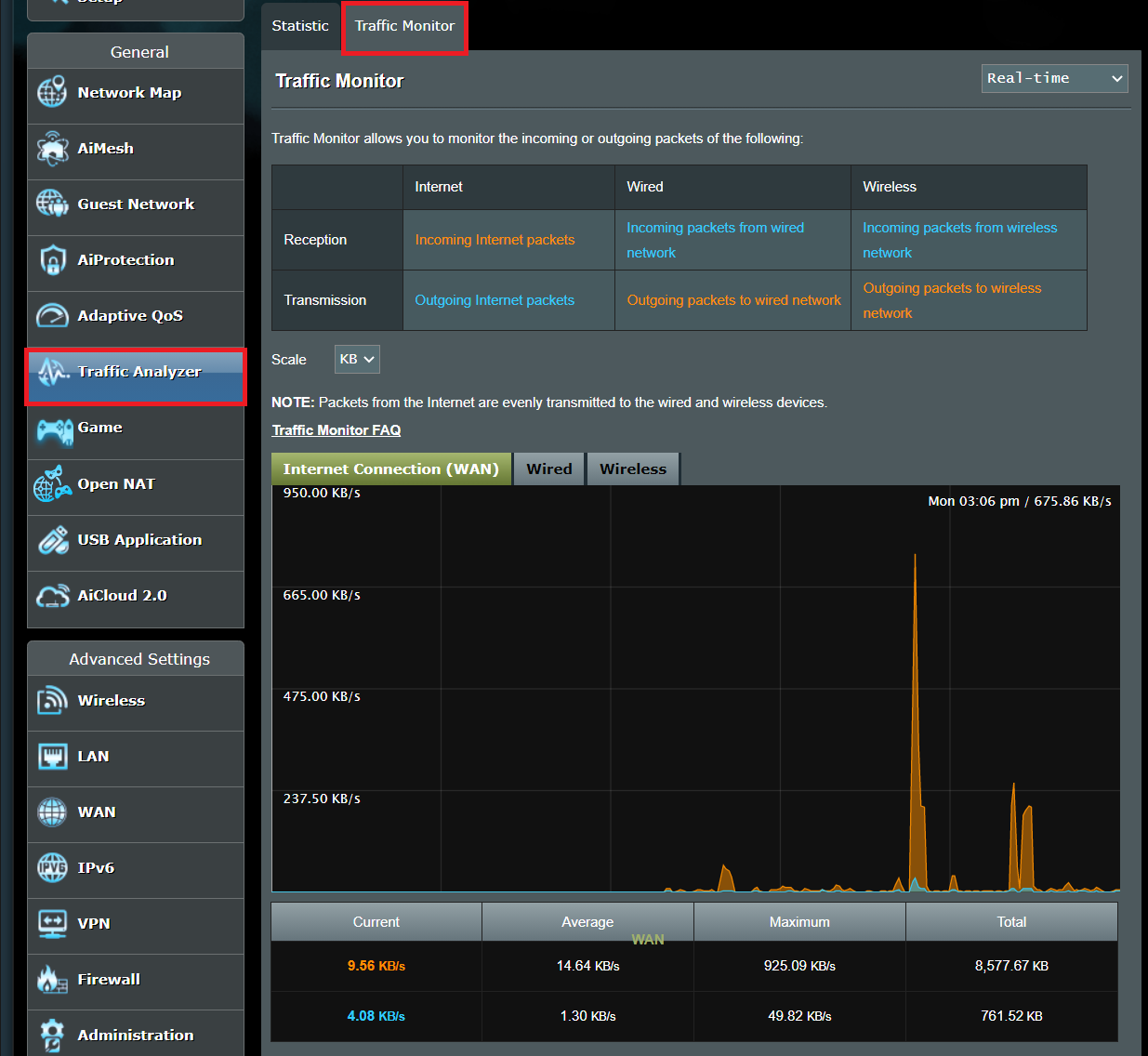
Log into your router:
192.168.1.1 or 192.168.0.1
Check:
Connected devices list
Unknown MAC addresses
Bandwidth usage spikes
DNS settings (should not point to unknown servers)
Red flags:
Devices communicating at 3AM constantly
Unknown DNS servers
High outbound traffic while idle
Advanced:
Install Pi-hole (network-level DNS logging)
Use OpenWRT/DD-WRT firmware for traffic inspection
2️⃣ OS-Level Permission Audit
Windows
Check:
Settings → Privacy & Security → App permissions
Background apps
Startup programs (Task Manager → Startup tab)
Advanced:
netstat -anoWindows Defender offline scan
Event Viewer logs
macOS
System Settings → Privacy & Security:
Full Disk Access
Screen Recording
Accessibility
Microphone & Camera
Then check:
Activity Monitor → Network tab
Android

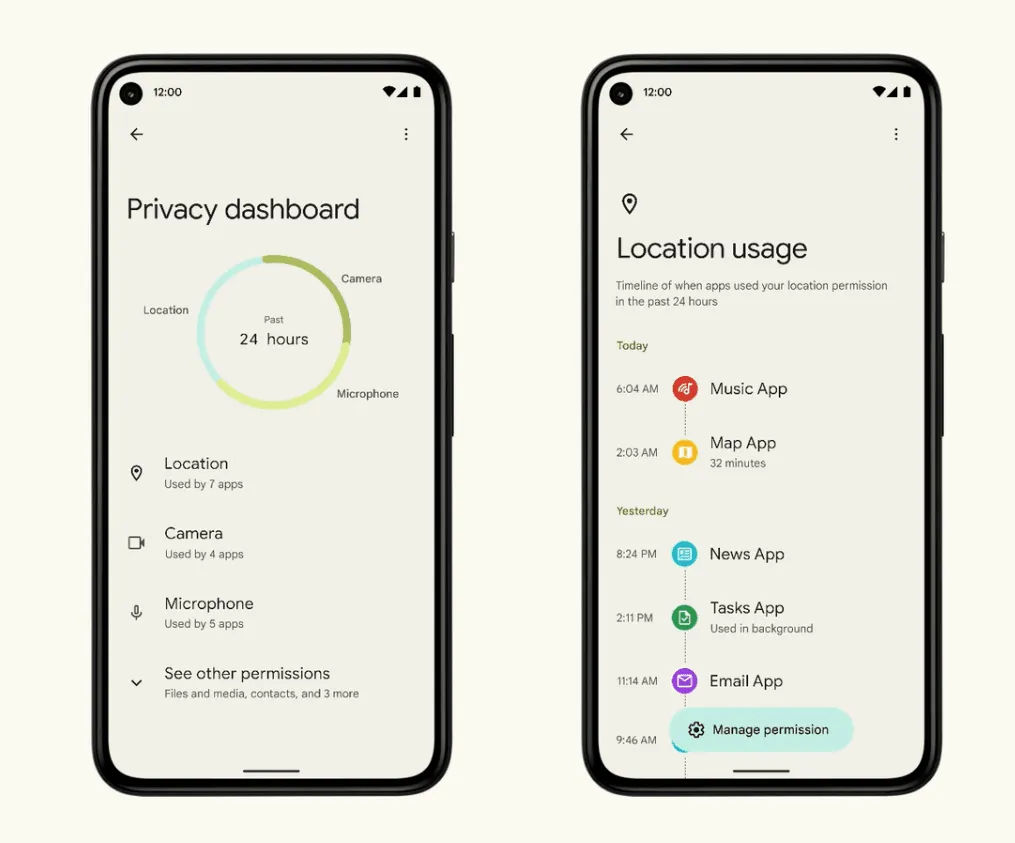

Settings → Privacy → Permission Manager
Check:
Apps with camera/mic access
Apps with “Special App Access”
Background data usage
Unknown sideloaded apps
iPhone
Settings → Privacy & Security → App Privacy Report
Check:
Frequency of mic/camera access
Domains contacted by apps
3️⃣ Installed Software & Firmware Audit
On Laptops
Remove unused software
Verify software publisher
Check digital signatures
Ensure BIOS/UEFI is updated from official site only
Check for:
Unknown browser extensions
VPNs you didn’t install
Remote desktop tools
Crypto miners
Browser:
chrome://extensions
4️⃣ Account-Level Audit (Often Overlooked)
Most tracking happens at account level, not device level.
Google Account
Security Activity
Devices logged in
Third-party apps with access
Ad personalization settings
Apple ID
Devices list
iCloud data access
App-specific passwords
Microsoft Account
Recent activity
Authorized apps
Recovery email changes
5️⃣ Hardware-Level Audit
More advanced but useful:
Check for unknown USB devices
Disable unused ports in BIOS
Disable boot from USB if unnecessary
Inspect webcam LED behavior
Use a physical camera cover
For SSD:
Use SMART monitoring tools
Check abnormal write patterns
6️⃣ Network Monitoring Tools (Advanced Layer)
If you want deeper inspection:
Wireshark (packet capture)
GlassWire (Windows traffic monitor)
Little Snitch (Mac outbound connection monitor)
NetGuard (Android firewall)
Pi-hole (DNS filtering)
These let you see:
Which apps contact which domains
Frequency of connections
Suspicious recurring patterns
7️⃣ How to Detect More Serious Compromise
Signs:
CPU high when idle
Battery draining fast
Unknown admin accounts
Antivirus disabled
Browser redirects
Unknown root certificates installed
If suspected:
Backup important data
Full OS reinstall
Reset router
Change passwords from clean device
Enable 2FA everywhere
8️⃣ Reality Check
For most users, risk is:
Phishing
Malicious apps
Data broker tracking
Ad tracking
Rarely:
Firmware-level spyware
Nation-state rootkits
Unless:
You are politically sensitive
Handling high-value IP
High net worth target
9️⃣ Minimal Practical Audit Routine (Monthly)
Here’s a clean repeatable routine:
Check router device list
Review app permissions
Remove unused apps
Update OS
Check account logins
Review browser extensions
Run malware scan
Review DNS settings
Total time: 30–45 minutes.
For You Specifically
Since you:
Work in education
Teach tech
Likely use multiple student-facing tools
May handle student data
Your highest risk area is:
Phishing
Credential reuse
Browser extension leakage
Compromised student project uploads
If you'd like, I can create:
A classroom-ready "Device Security Audit Lab" module
Or a more advanced forensic-level audit framework
Which depth do you want — practical user level or cybersecurity teaching level?